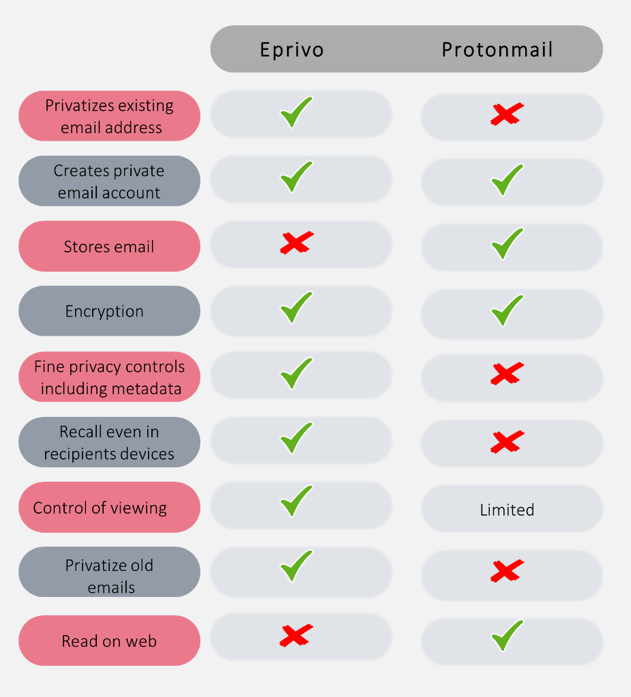
Sender-Controlled Private Email – Privacy Controls for Protection in the Cloud and Recipient’s Devices
 How are the sender-controlled private email features used? EPRIVO includes special privacy features that can be associated with each EPRIVO email we send. These features enable pioneering sender-control for private emails in both cloud and recipient devices. The sender retains ability to manage emails everywhere, even after they are sent.
How are the sender-controlled private email features used? EPRIVO includes special privacy features that can be associated with each EPRIVO email we send. These features enable pioneering sender-control for private emails in both cloud and recipient devices. The sender retains ability to manage emails everywhere, even after they are sent.
The availability of features depends on the type of subscription, but here we will discuss them in general. Privacy is essentially affected by both technical and socio-economic factors.
Read more